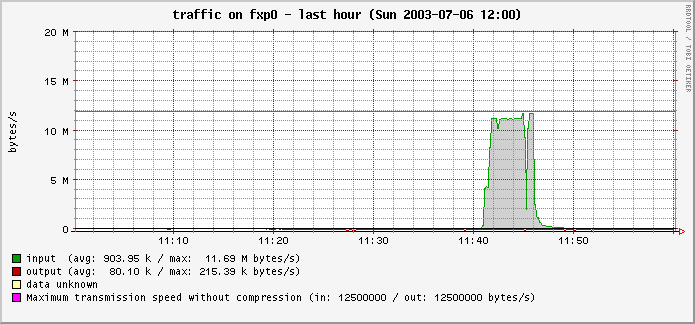
I had someone attempt a DOS attack against my public ET server tonight. It came in the form of a connect flood:
Client 410 connecting with 300 challenge ping
Client 413 connecting with 200 challenge ping
Client 413 connecting with 200 challenge ping
Client 413 connecting with 200 challenge ping
Client 413 connecting with 200 challenge ping
Client 410 connecting with 300 challenge ping
Client 413 connecting with 200 challenge ping
Multiply that by about 100,000 lines. This went on for a good hour, with about 25 attempts a second on average, occasionally spiking up to 50 or more.
Now, the good news is that the server blithely ignored this attack as it was going on, with gameplay completely unaffected even with a full (20-person) server. So kudos to Splash Damage for making the netcode bright enough to not succumb to this lame sort of behavior.
However, it would be nice if the server did one of two things (preferably both):
-
Automatically ignore an IP after a series of bogus connection attempts. That way the message doesn’t flood the console logs (which could be a problem if you’re running under a disk quota).
-
Show the IP in the connection message, so I can blackhole them at my firewall, or perhaps even pursue an investigation.